AWS Login: 7 Ultimate Tips for Secure & Fast Access
Logging into AWS doesn’t have to be complicated. Whether you’re a developer, sysadmin, or cloud newbie, mastering the AWS login process is your first step toward seamless cloud management. Let’s break it down—simply, securely, and smartly.
Understanding AWS Login: The Gateway to the Cloud

The AWS login is your entry point to one of the most powerful cloud ecosystems in the world. Amazon Web Services (AWS) provides over 200 fully featured services, from computing and storage to machine learning and analytics. But before you can deploy a server or analyze big data, you need to securely log in. The login process isn’t just about typing a username and password—it’s the foundation of your cloud security posture.
What Is AWS Login?
AWS login refers to the authentication process that allows users to access the AWS Management Console, Command Line Interface (CLI), or Software Development Kits (SDKs). It verifies your identity so AWS can determine what resources you’re allowed to use. This process is tightly integrated with AWS Identity and Access Management (IAM), which controls permissions and access policies.
Why Secure AWS Login Matters
A compromised AWS login can lead to data breaches, unauthorized resource usage, and even financial loss. According to a 2023 report by Palo Alto Networks, misconfigured IAM policies and weak login practices were responsible for 68% of cloud security incidents. That’s why understanding and securing your AWS login isn’t optional—it’s essential.
“The security of your cloud environment starts with a single login. Get it wrong, and everything else is at risk.” — AWS Security Best Practices Guide
AWS Login Methods: Console, CLI, and SDKs
There are multiple ways to perform an AWS login, each suited for different use cases. Choosing the right method depends on your role, workflow, and security requirements.
AWS Management Console Login
The most common AWS login method is through the AWS Management Console, a web-based interface. To log in:
- Navigate to https://aws.amazon.com/console/
- Enter your AWS account email address or root user credentials
- Input your password
- Complete multi-factor authentication (MFA) if enabled
Once logged in, you gain access to all AWS services through a graphical user interface. This method is ideal for beginners and administrators managing resources manually.
AWS CLI Login (Using IAM Credentials)
For developers and DevOps engineers, the AWS CLI offers a faster, scriptable way to interact with AWS. However, the CLI doesn’t use a traditional “login” command. Instead, you configure credentials using:
- Access Key ID and Secret Access Key
- Session tokens (for temporary credentials)
- Named profiles for multiple accounts
Run aws configure to set up your credentials locally. These are stored in ~/.aws/credentials. Never hardcode credentials in scripts—use IAM roles or temporary tokens instead.
Programmatic Access via SDKs
AWS SDKs (for Python, JavaScript, Java, etc.) allow applications to interact with AWS services programmatically. The login process here is handled through credential providers that fetch credentials from:
- Environment variables
- Shared credential files
- EC2 instance roles
- Web Identity Federation
For example, in Python’s Boto3, you don’t explicitly “log in.” Instead, the SDK automatically sources credentials from the environment or IAM roles attached to the EC2 instance.
Step-by-Step Guide to AWS Login for Beginners
If you’re new to AWS, the login process can feel overwhelming. Here’s a clear, step-by-step guide to help you log in safely and correctly.
Step 1: Go to the AWS Sign-In Page
Open your browser and go to https://aws.amazon.com/console/. You’ll see two options:
- Root User Login: Use the email and password you used to create the AWS account.
- IAM User Login: For users created under IAM with limited permissions.
Always avoid using the root user for daily tasks. Instead, create IAM users with least-privilege permissions.
Step 2: Enter Your Credentials
If you’re logging in as an IAM user, enter your account ID or alias and your IAM username. Then, type your password. Make sure you’re using a strong, unique password. AWS enforces password policies that can be customized in IAM settings.
Step 3: Enable and Use MFA
After entering your password, if MFA is enabled, you’ll be prompted for a code from your authenticator app (like Google Authenticator or Authy) or a hardware key. This adds a critical second layer of security. AWS strongly recommends enabling MFA for all users, especially the root account.
Securing Your AWS Login: Best Practices
Security should be the top priority when managing AWS login access. A single compromised credential can lead to massive data exposure or cryptojacking attacks. Follow these best practices to lock down your AWS login process.
Use IAM Roles Instead of Long-Term Credentials
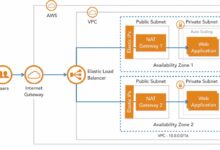
Long-term access keys are a major security risk. Instead, use IAM roles that provide temporary security credentials. For example, EC2 instances can assume roles without storing access keys. This follows the principle of least privilege and reduces the attack surface.
Enforce Multi-Factor Authentication (MFA)
MFA is one of the most effective ways to secure your AWS login. Even if a password is leaked, an attacker can’t log in without the second factor. You can enforce MFA through IAM policies. For example:
- Require MFA for console access
- Require MFA to change account settings
- Use FIDO2 security keys for phishing-resistant MFA
AWS supports virtual MFA devices, U2F security keys, and hardware MFA devices.
Rotate Credentials Regularly
Regularly rotate access keys, passwords, and certificates. AWS allows you to set password rotation policies in IAM. For access keys, automate rotation using AWS Lambda or third-party tools. Never reuse passwords across accounts or services.
“Security is not a product, but a process. Your AWS login is the first checkpoint in that process.” — AWS Chief Security Officer
Troubleshooting Common AWS Login Issues
Even experienced users face login problems. Here’s how to diagnose and fix the most common AWS login issues.
“Invalid Credentials” Error
This error usually means:
- Wrong username or password
- Using root credentials when IAM user is expected (or vice versa)
- Account is locked due to multiple failed attempts
Solution: Double-check your login URL and credentials. Reset your password if needed. If you’re an IAM user, contact your administrator to verify your account status.
“Access Denied” After Login
You may log in successfully but see “Access Denied” when accessing services. This is a permissions issue, not a login problem. Your IAM user lacks the necessary policies. Contact your AWS admin to attach the correct IAM policies (e.g., AmazonS3ReadOnlyAccess, PowerUserAccess).
MFA Not Working?
If your MFA device isn’t generating valid codes:
- Check device time synchronization (critical for TOTP)
- Re-scan the QR code or re-enter the secret key
- Contact AWS Support if the device is lost or damaged
You can also set up backup MFA devices for emergency access.
Advanced AWS Login: SSO, Federation, and SAML
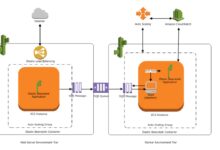
For enterprises, managing individual AWS logins for hundreds of users isn’t scalable. That’s where AWS Single Sign-On (SSO) and identity federation come in.
What Is AWS SSO?
AWS Single Sign-On (SSO) allows users to log in once and access multiple AWS accounts and business applications. It integrates with Microsoft Active Directory, Okta, Azure AD, and other identity providers. With AWS SSO, you eliminate the need for separate IAM users in each account.
Federated Login Using SAML 2.0
SAML (Security Assertion Markup Language) enables federated identity. Your organization’s identity provider (IdP) authenticates the user and sends a SAML assertion to AWS. AWS then grants temporary credentials based on IAM roles. This is ideal for large enterprises with existing identity systems.
Using OpenID Connect (OIDC) for Web Apps
OIDC is perfect for web and mobile apps that need AWS access. Users log in via Google, Facebook, or Amazon, and AWS grants temporary credentials. This is commonly used with Amazon Cognito for user pools and identity federation.
Automating AWS Login with Scripts and Tools
Manual logins are fine for occasional use, but automation is key for DevOps and CI/CD pipelines. Here’s how to automate AWS login securely.
Using AWS CLI with Named Profiles
Create multiple profiles for different environments (dev, staging, prod):
aws configure --profile dev
aws configure --profile prodThen, use them in commands:
aws s3 ls --profile devThis avoids credential conflicts and improves security through separation of duties.
Temporary Credentials with AWS STS
The AWS Security Token Service (STS) provides temporary, limited-privilege credentials. Use sts assume-role to switch roles programmatically:
aws sts assume-role --role-arn arn:aws:iam::123456789012:role/DevRole --role-session-name DevSessionThis is ideal for cross-account access and automation scripts.
CI/CD Integration with GitHub Actions
In GitHub Actions, use the aws-actions/configure-aws-credentials action to securely inject temporary credentials:
- name: Configure AWS Credentials
uses: aws-actions/configure-aws-credentials@v1
with:
aws-access-key-id: ${{ secrets.AWS_ACCESS_KEY_ID }}
aws-secret-access-key: ${{ secrets.AWS_SECRET_ACCESS_KEY }}
aws-region: us-east-1Never store long-term keys in repositories. Use IAM roles for GitHub Actions instead when possible.
Monitoring and Auditing AWS Login Activity
Knowing who logged in, when, and from where is critical for security and compliance. AWS provides tools to monitor and audit all login events.
Using AWS CloudTrail for Login Logs
AWS CloudTrail logs all AWS API calls, including console and CLI logins. Look for events like ConsoleLogin, AssumeRole, and GetSessionToken. You can filter logs by user, IP address, or time range.
Setting Up CloudWatch Alarms for Suspicious Logins
Create CloudWatch alarms to notify you of failed login attempts or logins from unusual locations. For example:
- More than 5 failed logins in 10 minutes
- Login from a country not in your allowed list
- Root account login (which should be rare)
Use AWS EventBridge to trigger automated responses, like disabling a user or sending an alert.
Generating IAM Credential Reports
AWS IAM Credential Reports provide a snapshot of all users and their credential status. You can check:
- Which users have passwords enabled
- Which users have MFA enabled
- When access keys were last used
Download the report from the IAM console or via CLI: aws iam generate-credential-report.
What is the safest way to perform AWS login?
The safest way is to use AWS Single Sign-On (SSO) with multi-factor authentication (MFA) and federated identity. Avoid using root credentials. Instead, use IAM roles with temporary credentials and enforce least-privilege access policies.
Can I log in to AWS without a password?
Yes. You can use federated login via SAML or OpenID Connect, where your organization’s identity provider handles authentication. Additionally, EC2 instances can use IAM roles to access AWS services without any login credentials.
How do I recover my AWS login if I’m locked out?
If you’re locked out of an IAM user account, an administrator can reset your password. If you’re locked out of the root account, use the “Forgot Password” option and verify your identity via email or phone. Always keep root account recovery contacts up to date.
Is AWS CLI considered a login method?
Not in the traditional sense. The AWS CLI doesn’t have a login command. Instead, it uses stored credentials (access keys, session tokens) or retrieves temporary credentials from IAM roles. Configuring the CLI with aws configure is the closest equivalent to logging in.
How often should I rotate my AWS login credentials?
AWS recommends rotating access keys every 90 days. Passwords should follow your organization’s policy, typically 60-90 days. Use automated tools or AWS Lambda functions to rotate keys and reduce human error.
Mastering AWS login is more than just accessing a dashboard—it’s about building a secure, scalable, and auditable cloud foundation. From basic console access to advanced federation and automation, every login method plays a role in your overall cloud strategy. By following best practices like enabling MFA, using IAM roles, and monitoring login activity, you protect your data, comply with regulations, and empower your team to innovate safely. Whether you’re a solo developer or part of a global enterprise, a smart AWS login process is your first line of defense and your gateway to the cloud’s full potential.
Recommended for you 👇
Further Reading: